Fortum’s Zero Trust Adoption Journey IT/OT Convergence and Strategic Business Drivers Bruno Amaro Almeida VP, IT Operations September 2024
Slide 1

Slide 2
Enabling Fortum’s transformation and success through efficient use of data and digital solutions Generation, Trading and Asset Optimization District Heating, Recycling & Waste Consumer Solutions Enterprise 2 … … Innovation & Venturing
Slide 3

IT STRATEGIC PRIORITIES Customer Centric Cost Efficient Secure and Reliable
Slide 4
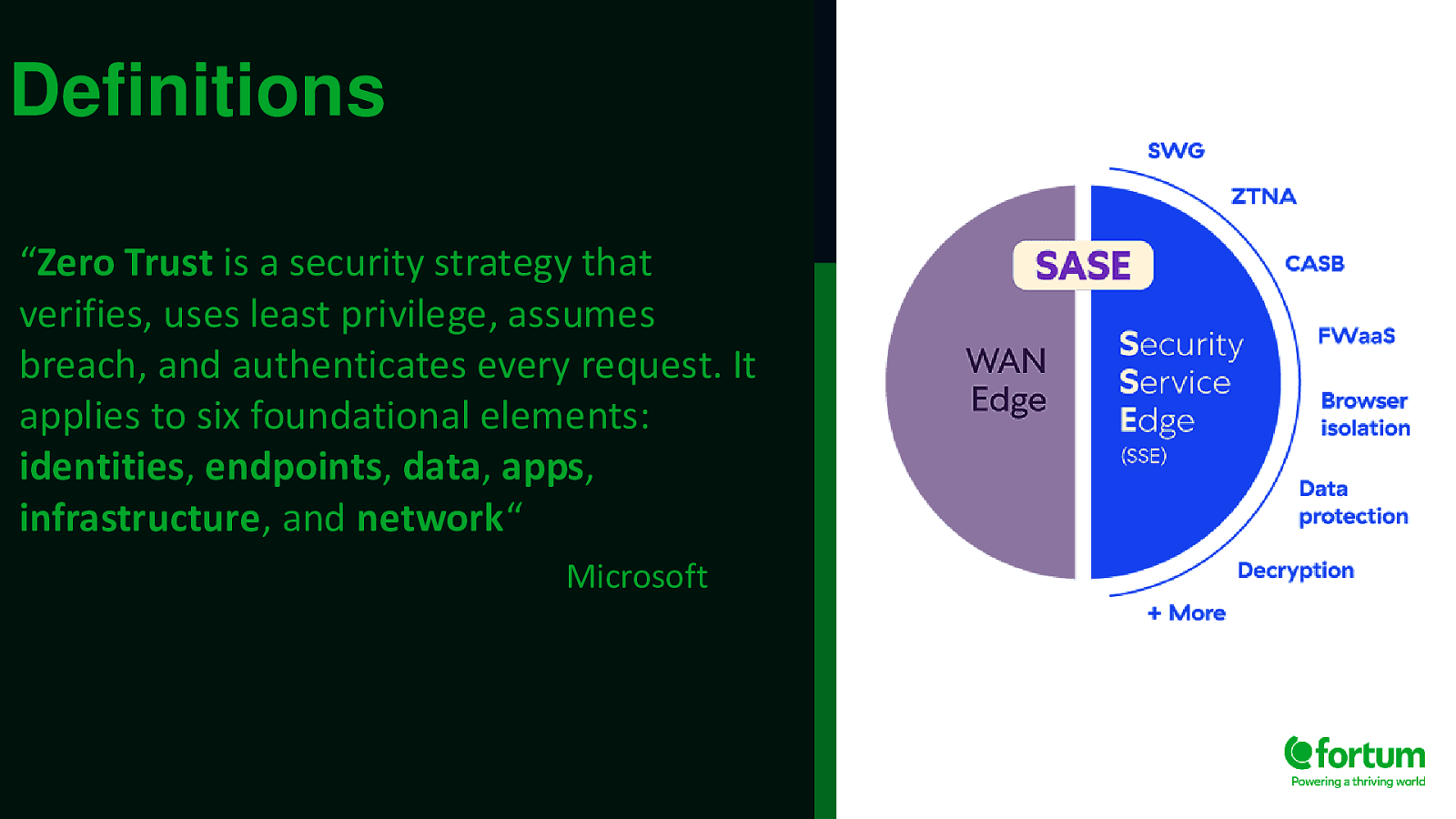
Definitions “Zero Trust is a security strategy that verifies, uses least privilege, assumes breach, and authenticates every request. It applies to six foundational elements: identities, endpoints, data, apps, infrastructure, and network“ Microsoft
Slide 5
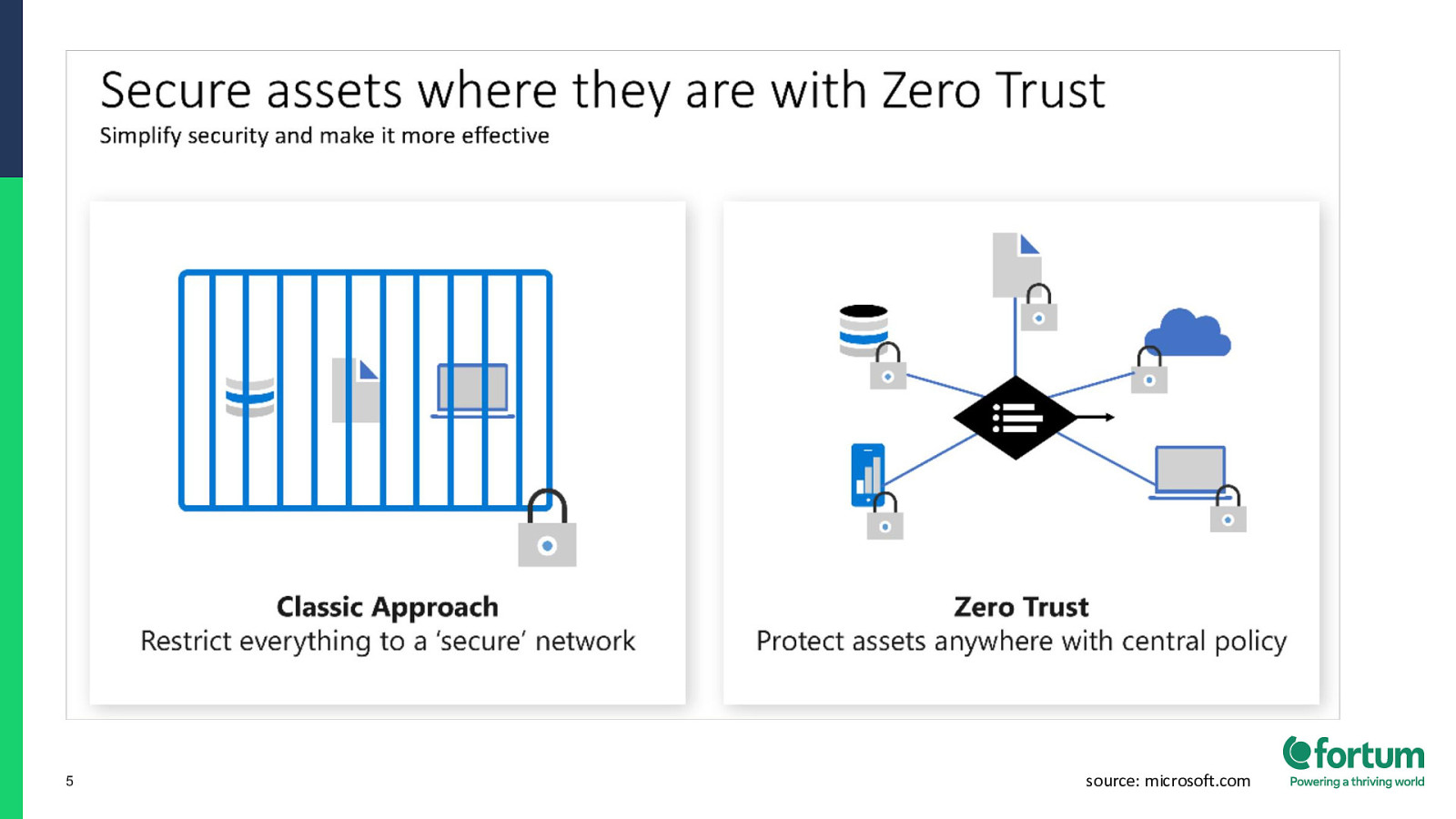
5 source: microsoft.com
Slide 6
Which type of IT project is a Zero Trust Adoption? 6 Cyber Security Employee Digital Experience Network & Connectivity Infrastructure & Platform
Slide 7
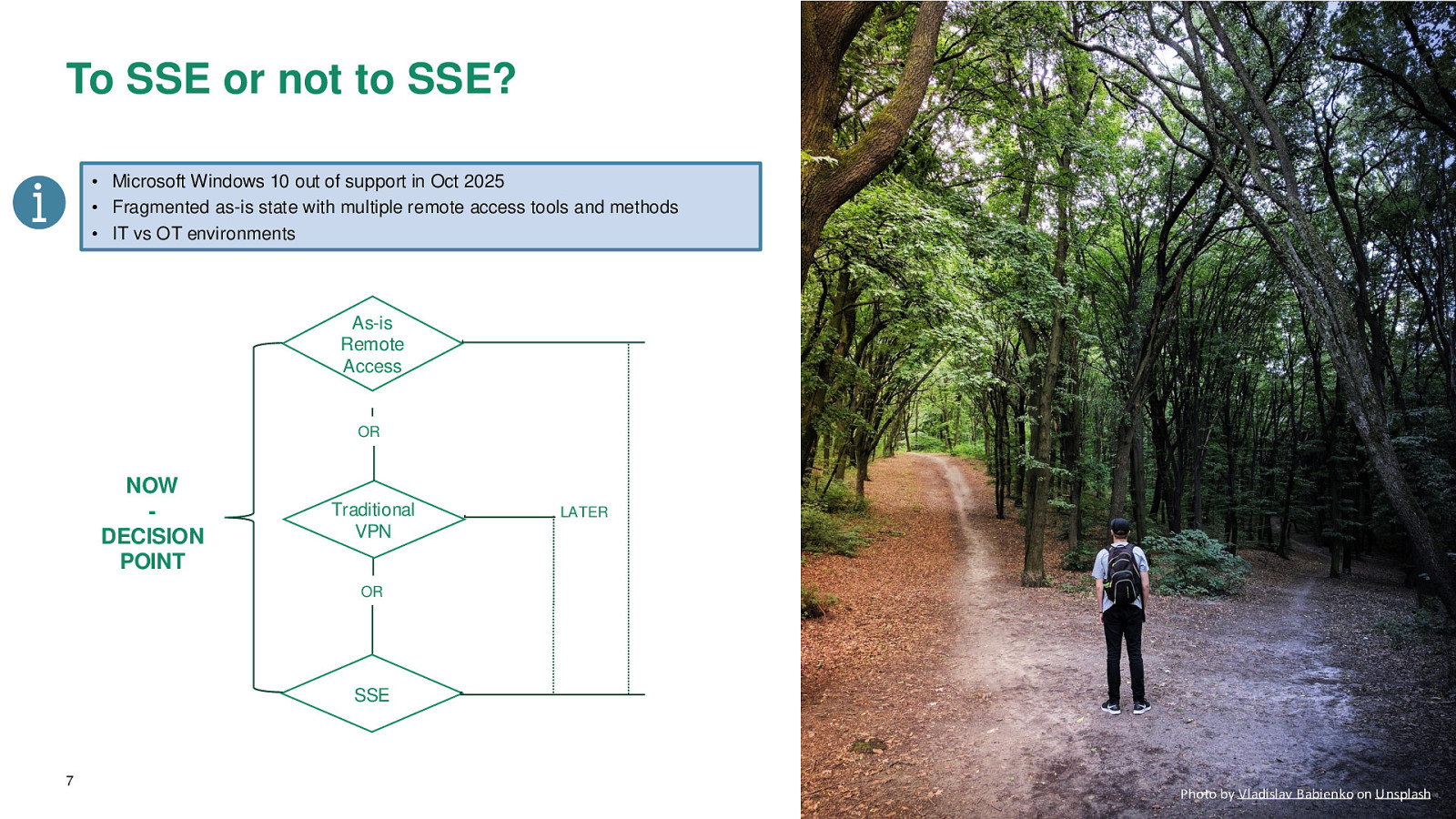
To SSE or not to SSE? • Microsoft Windows 10 out of support in Oct 2025 • Fragmented as-is state with multiple remote access tools and methods • IT vs OT environments As-is Remote Access OR NOW DECISION POINT Traditional VPN LATER OR SSE 7 Photo by Vladislav Babienko on Unsplash
Slide 8
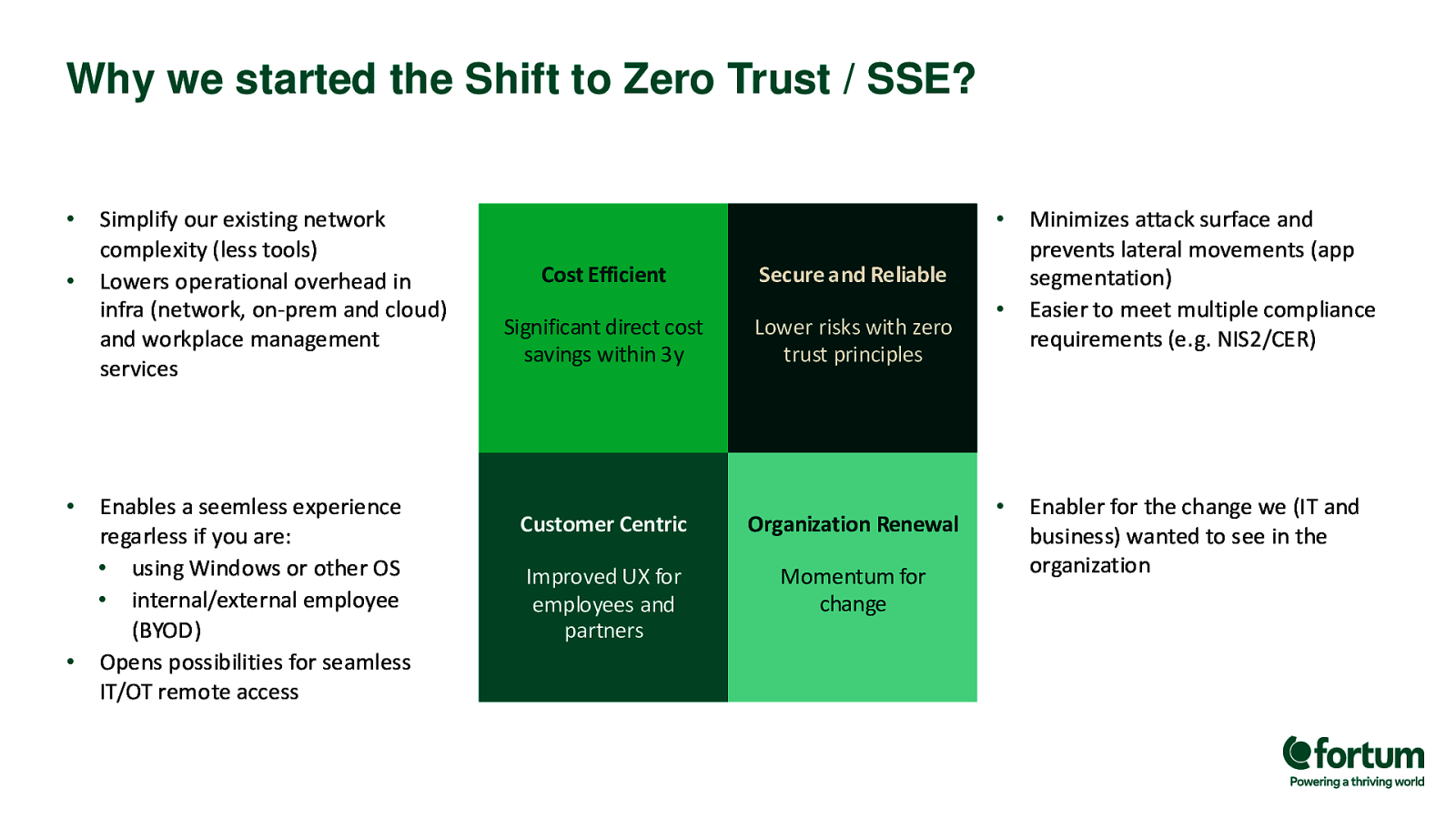
Why we started the Shift to Zero Trust / SSE? • • • Simplify our existing network complexity (less tools) Lowers operational overhead in infra (network, on-prem and cloud) and workplace management services Enables a seemless experience regarless if you are: • using Windows or other OS • internal/external employee (BYOD) • Opens possibilities for seamless IT/OT remote access • Cost Efficient Secure and Reliable Significant direct cost savings within 3y Lower risks with zero trust principles Customer Centric Organization Renewal Improved UX for employees and partners Momentum for change • • Minimizes attack surface and prevents lateral movements (app segmentation) Easier to meet multiple compliance requirements (e.g. NIS2/CER) Enabler for the change we (IT and business) wanted to see in the organization
Slide 9

Our Zero Trust Adoption Journey OT access and privileged remote access enhanced OT use-cases and automation Internal and External Browser based Access extended remote access, priviledge access mgmt, combine experience with operational data Remote access for “office use” (Windows 11 Readiness) Employee remote access, virtual desktops and hardware Photo by LOGAN WEAVER | @LGNWVR on Unsplash
Slide 10
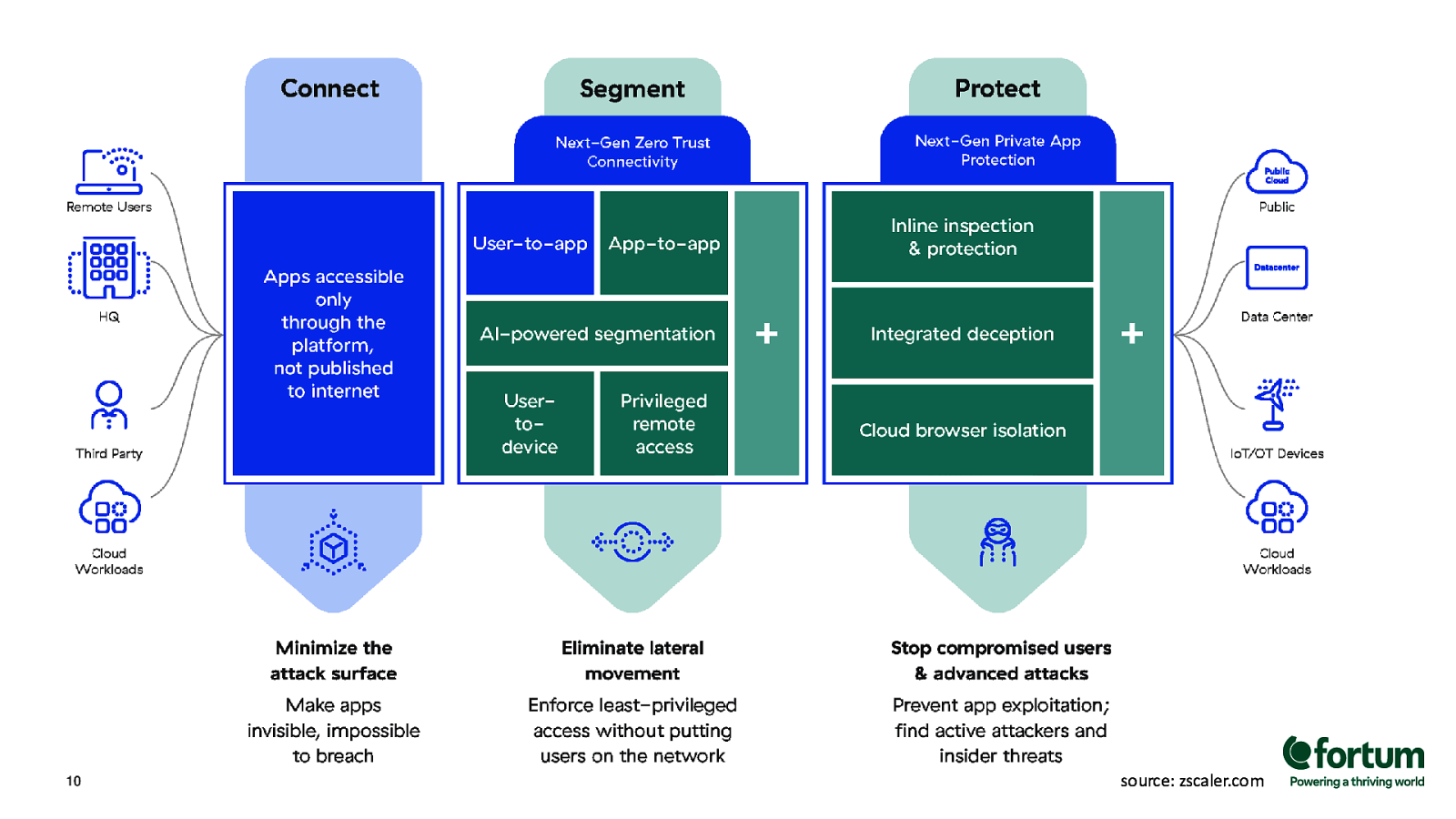
10 source: zscaler.com
Slide 11
Lessons and Key Considerations Employee Personas and Developer Experience 11 Mergers, Acquisitions and Divestments (MAD) Platform Engineering and Automation Capabilities
Slide 12

Questions & Answers Bruno Amaro Almeida VP, IT Operations brunoamaro.com