From DevOps to DevSecOps How Establishing a Threat Modeling Process Can Help You Transition NDC Oslo June 2020 Bruno Amaro Almeida BERLIN · HELSINKI · LONDON · MUNICH · OSLO · STOCKHOLM · TAMPERE @bruno_amaro Photo by Praveesh Palakeel on Unsplash
Slide 1

Slide 2
Thank you! Kiitos! Danke! Tack! Hello! Bruno Amaro Almeida P RINC IP AL ARC HITE C T & ADV ISOR Cloud, DevOps, Security, Data Engineering & AI Reach out on: @bruno_amaro @brunoamaroalmeida BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE
Slide 3
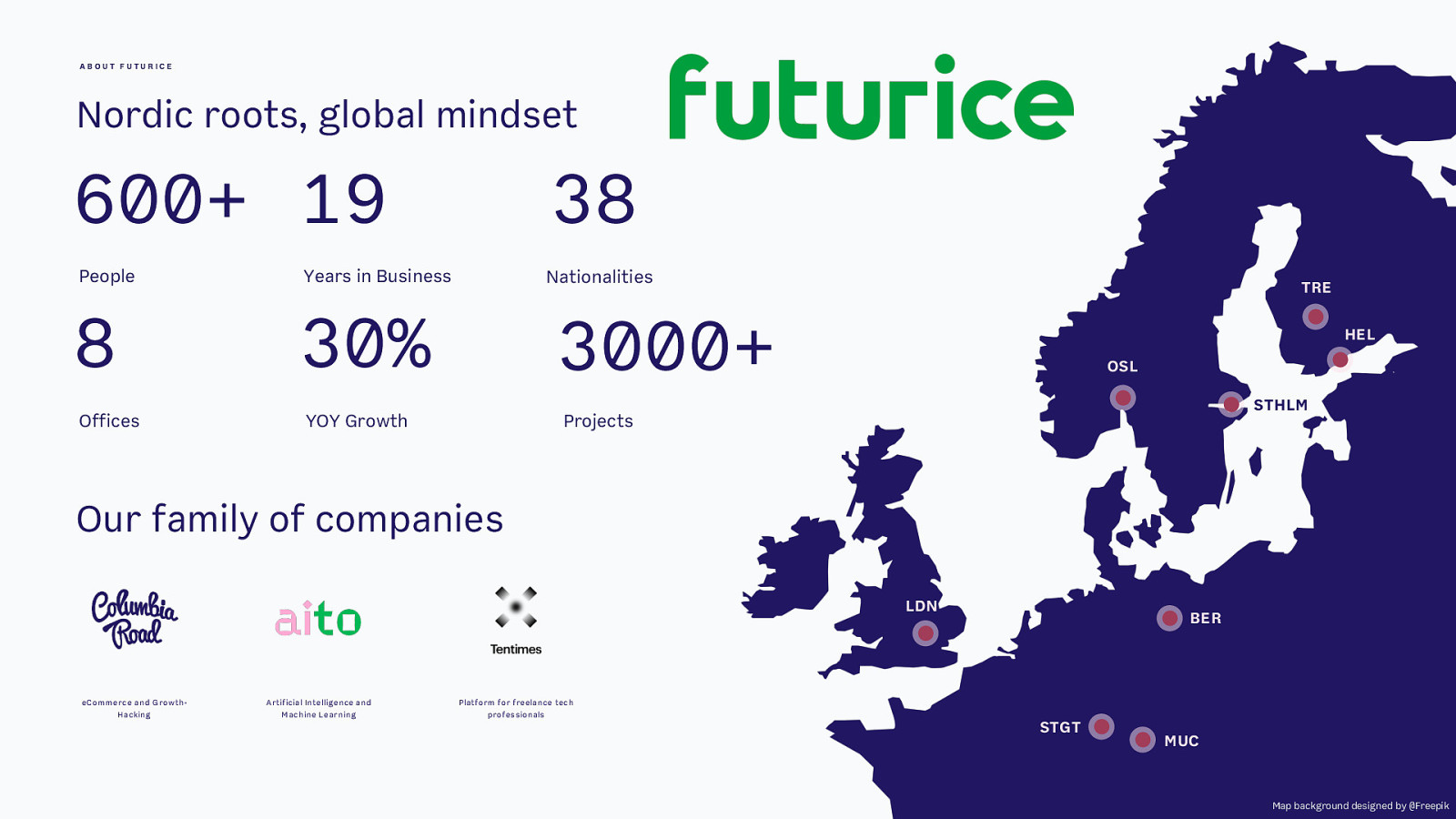
ABOUT FUTURICE Nordic roots, global mindset 38 600+ 19 People 8 Offices Years in Business Nationalities 30% TRE 3000+ YOY Growth HEL OSL STHLM Projects Our family of companies LDN eCom m erce and Grow thHacking Artificial Intelligence and M achine Learning BER Platform for freelance tech professionals STGT MUC Map background designed by @Freepik
Slide 4
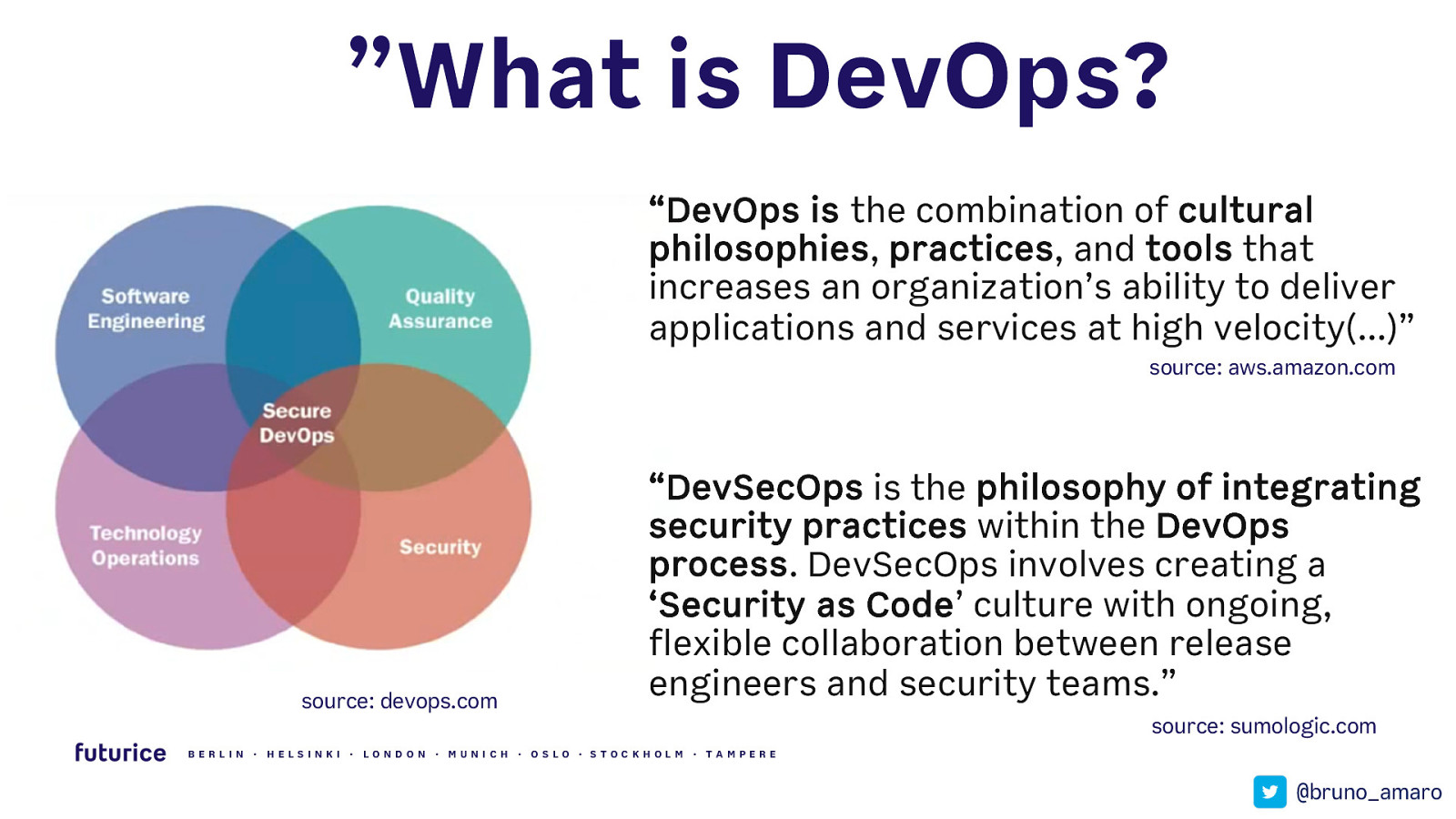
”What is DevOps? “DevOps is the combination of cultural philosophies, practices, and tools that increases an organization’s ability to deliver applications and services at high velocity(…)” source: aws.amazon.com source: devops.com “DevSecOps is the philosophy of integrating security practices within the DevOps process. DevSecOps involves creating a ‘Security as Code’ culture with ongoing, flexible collaboration between release engineers and security teams.” source: sumologic.com BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 5
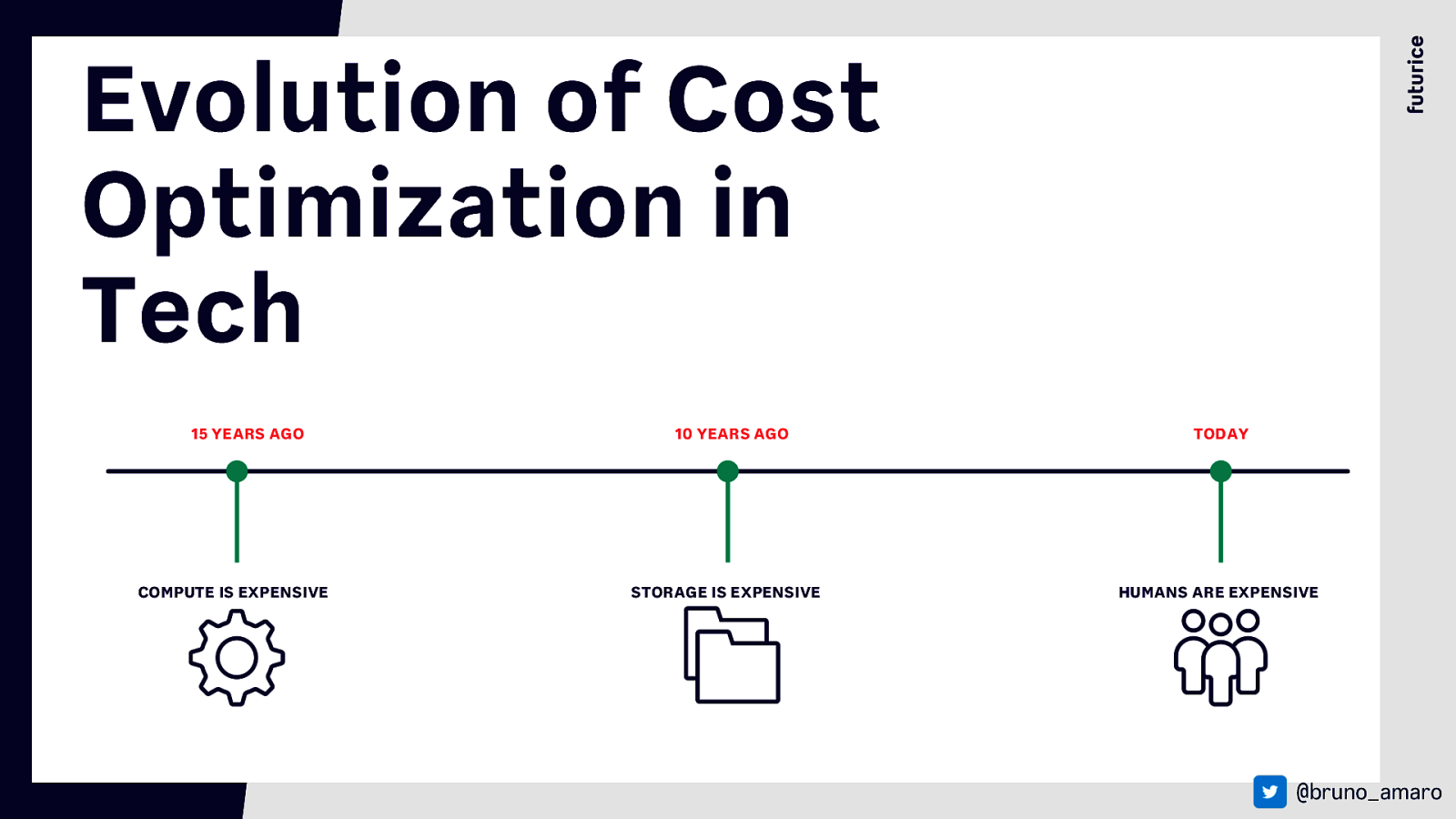
Evolution of Cost Optimization in Tech 15 YEARS AGO COMPUTE IS EXPENSIVE 10 YEARS AGO STORAGETITLE IS EXPENSIVE TODAY HUMANS ARE EXPENSIVE @bruno_amaro
Slide 6
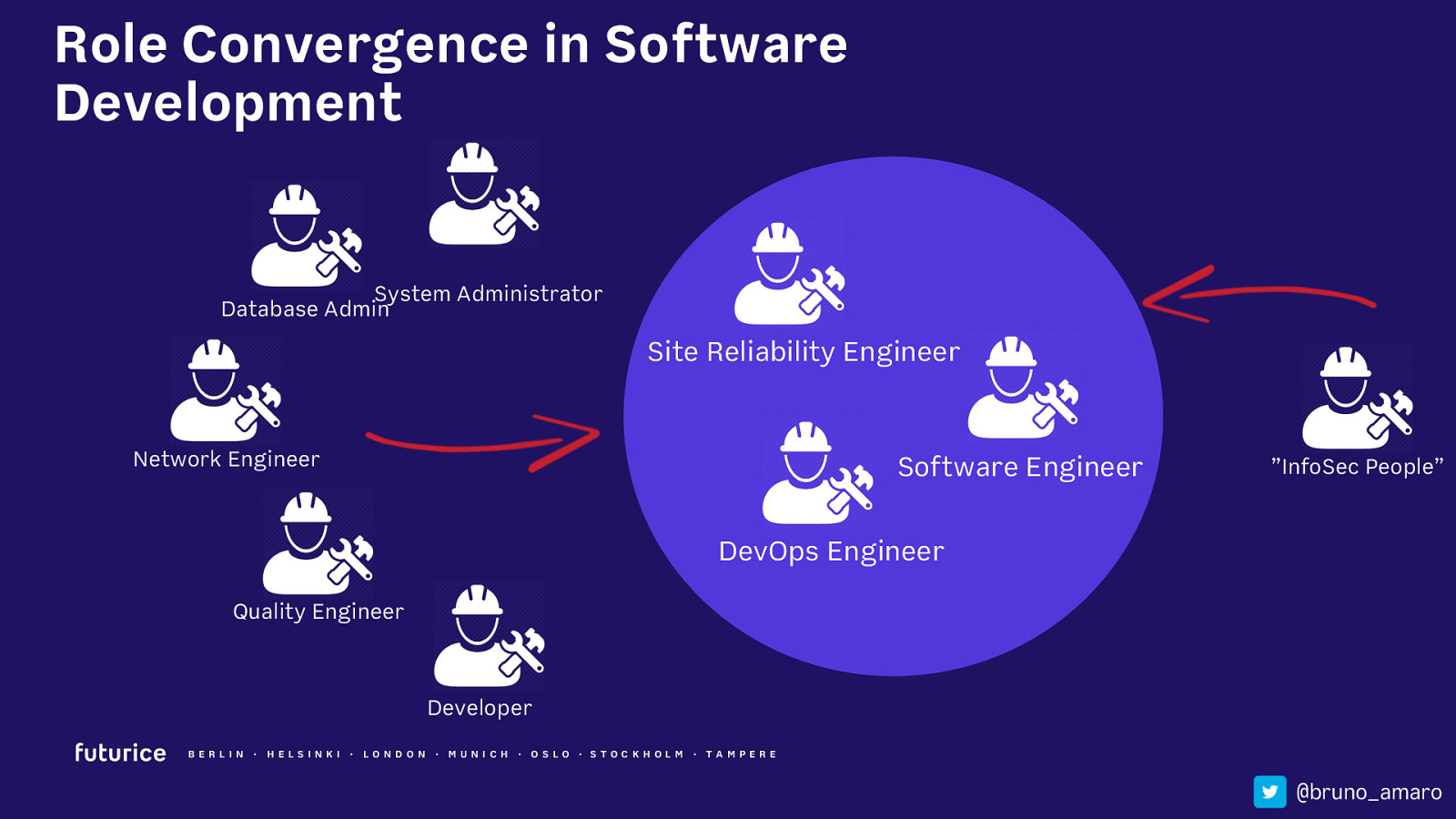
Role Convergence in Software Development System Administrator Database Admin Site Reliability Engineer Network Engineer Software Engineer ”InfoSec People” DevOps Engineer Quality Engineer Developer BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 7
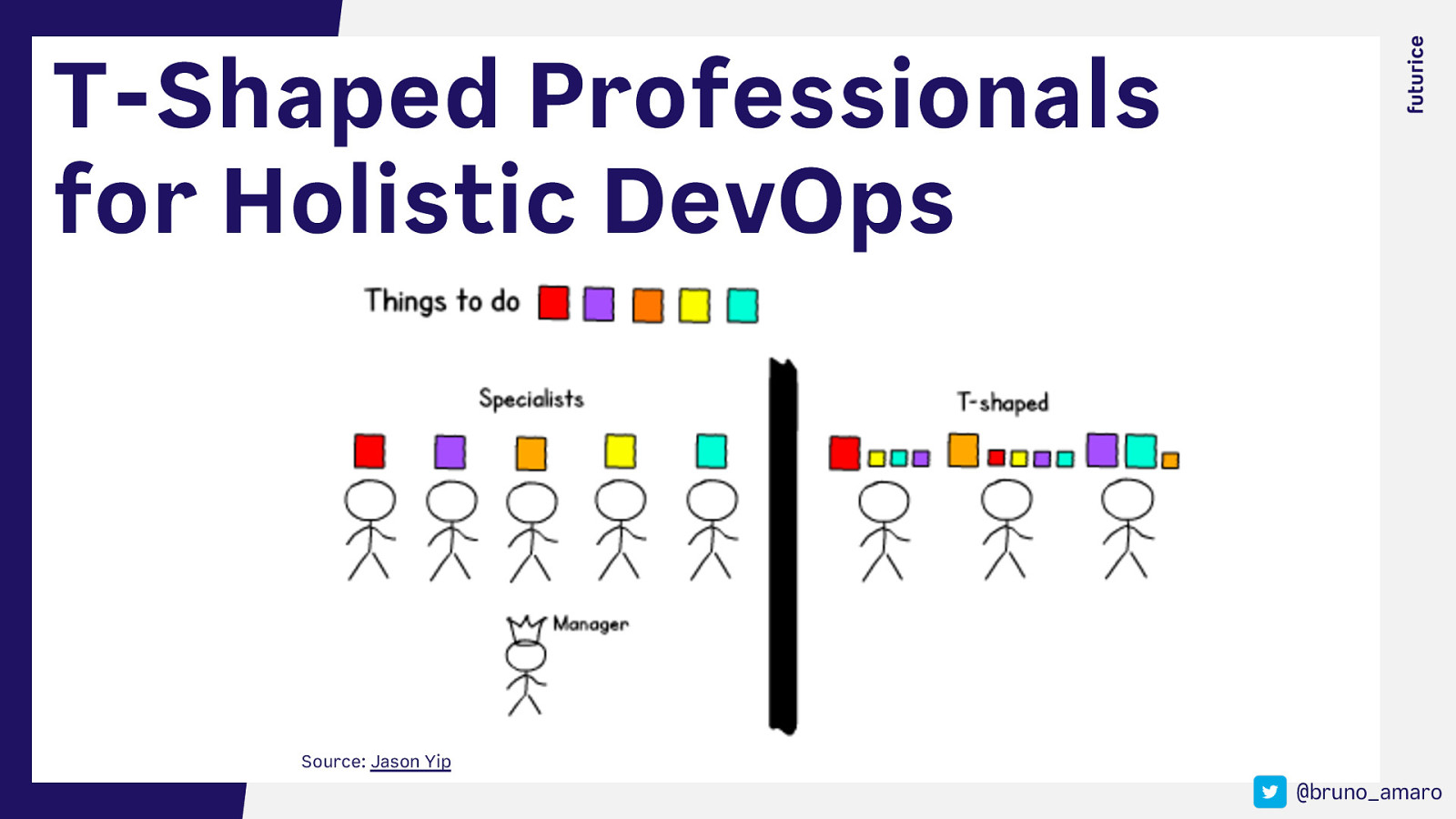
T-Shaped Professionals for Holistic DevOps Source: Jason Yip @bruno_amaro
Slide 8

How Engineers Typically ”Sell” Security
Slide 9

Why should you care about DevSecOps? Having DevSecOps practices (e.g. Threat Modeling) in our organization enables us FASTER TIME TO MARKET • • Documentation up to date Faster Feature Delivery COST SAVINGS AND REDUCED HIGHER CUSTOMER ENGANGEMENT CREDIBILITY AND NEW BUSINESS OPERATIONAL COST AND SATISFACTION OPORTUNITIES • Lean Security Audits • Less Bugs and Vulnerabilities • Better User Experience understanding • Compliance (ISO 27001, GDPR) @bruno_amaro
Slide 10

“ “Threat modelling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.” source: owasp.org Different Methodologies • VAST: Visual, Agile & Simple Threat Modeling • PASTA: The Process for Attack Simulation & Threat Analysis • TRIKE • STRIDE • … @bruno_amaro
Slide 11

Threat Modelling Meet STRIDE @bruno_amaro
Slide 12
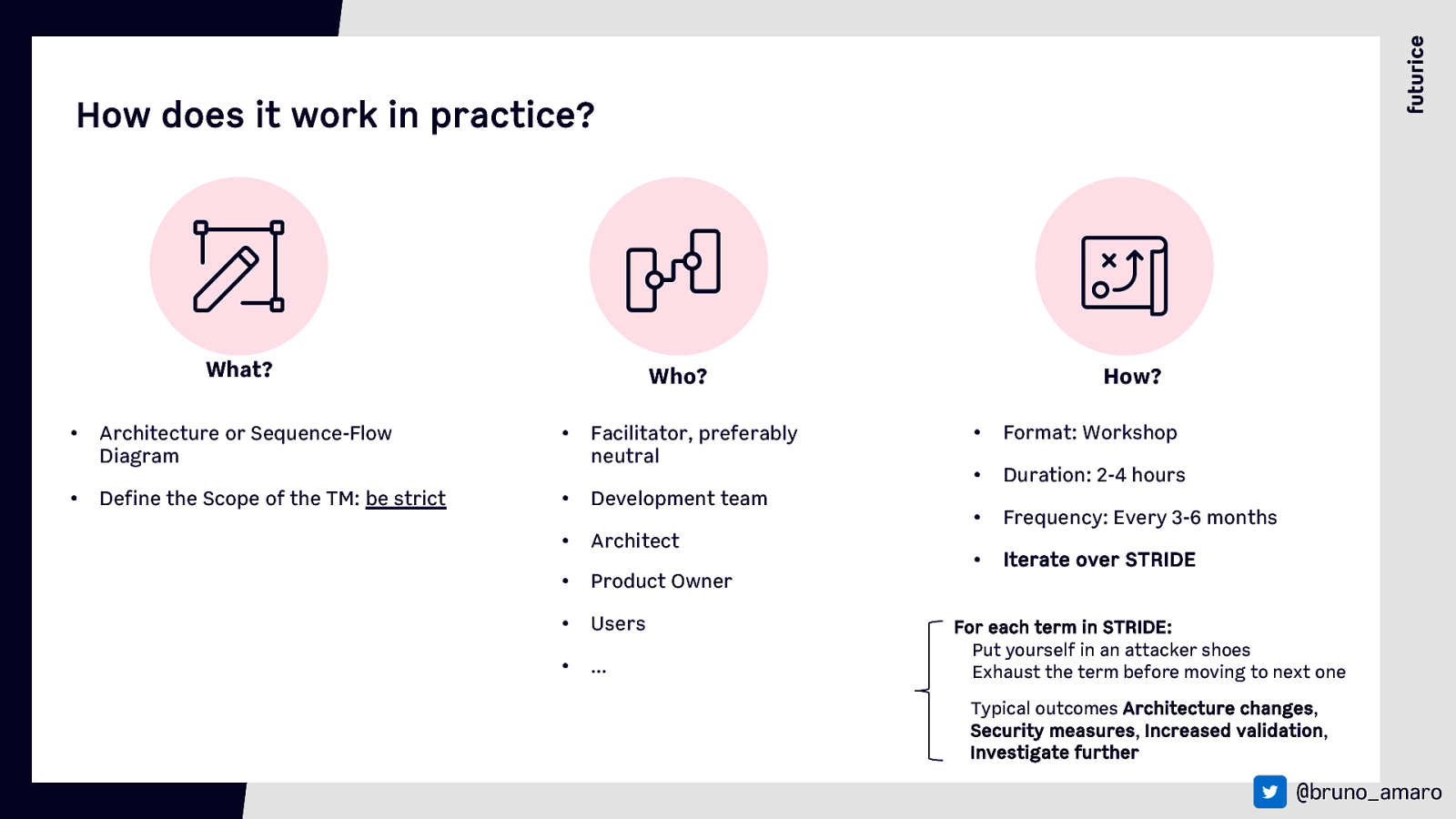
How does it work in practice? What? Who? • Architecture or Sequence-Flow Diagram • Facilitator, preferably neutral • Define the Scope of the TM: be strict • Development team • Architect • Product Owner • Users • … How? • Format: Workshop • Duration: 2-4 hours • Frequency: Every 3-6 months • Iterate over STRIDE For each term in STRIDE: Put yourself in an attacker shoes Exhaust the term before moving to next one Typical outcomes Architecture changes, Security measures, Increased validation, Investigate further @bruno_amaro
Slide 13
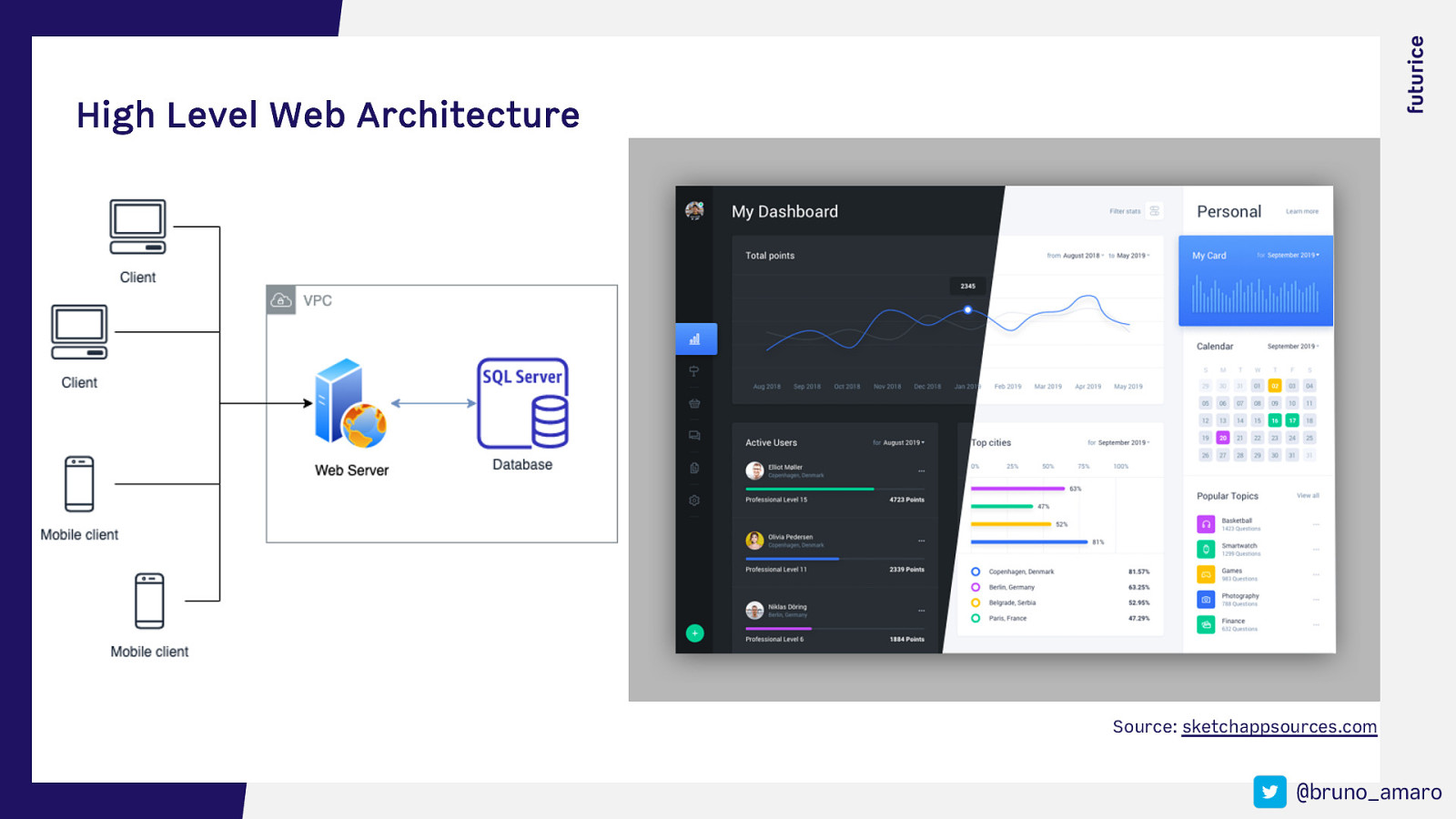
High Level Web Architecture Source: sketchappsources.com @bruno_amaro
Slide 14
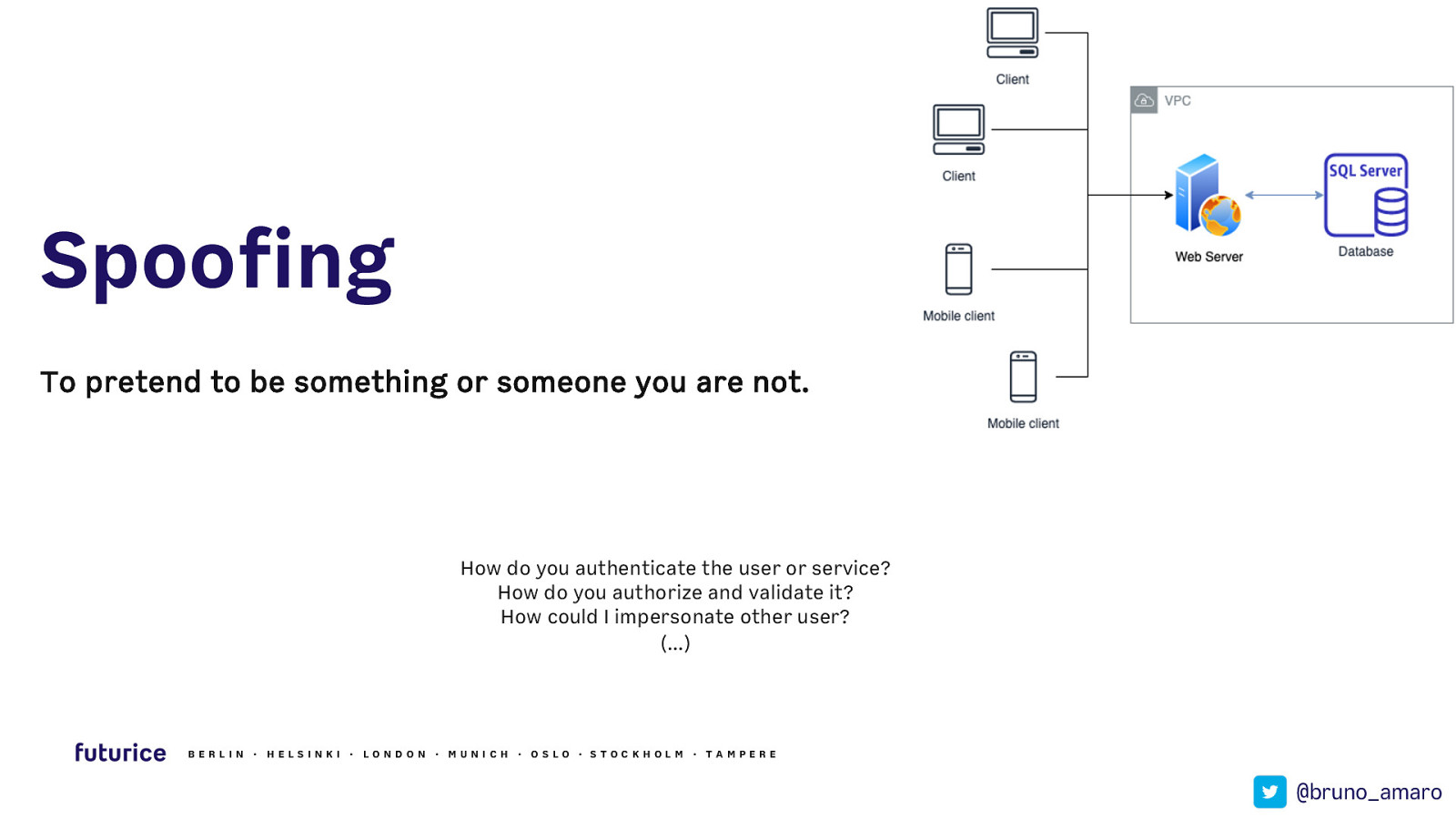
Spoofing To pretend to be something or someone you are not. How do you authenticate the user or service? How do you authorize and validate it? How could I impersonate other user? (…) BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 15
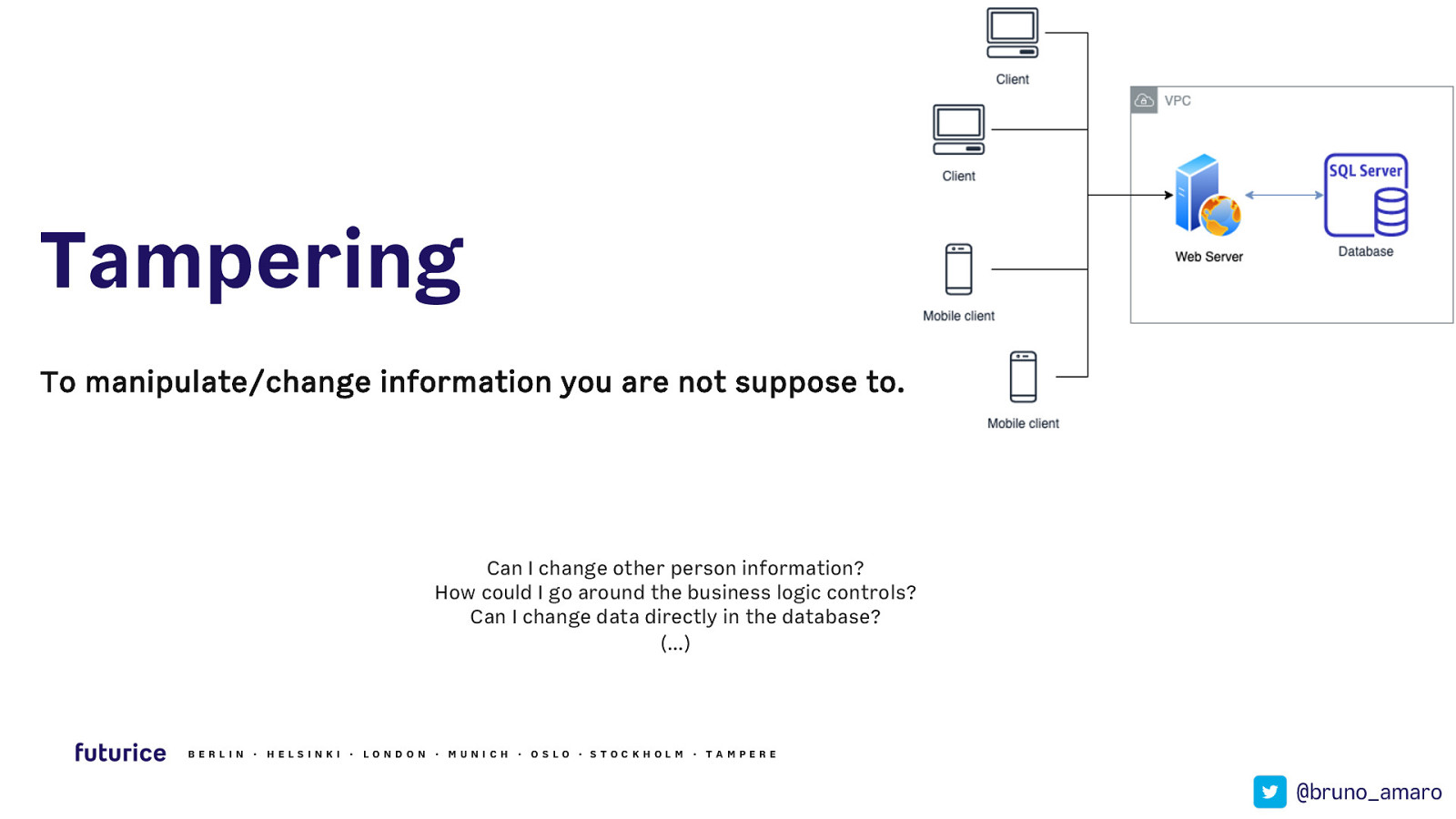
Tampering To manipulate/change information you are not suppose to. Can I change other person information? How could I go around the business logic controls? Can I change data directly in the database? (…) BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 16
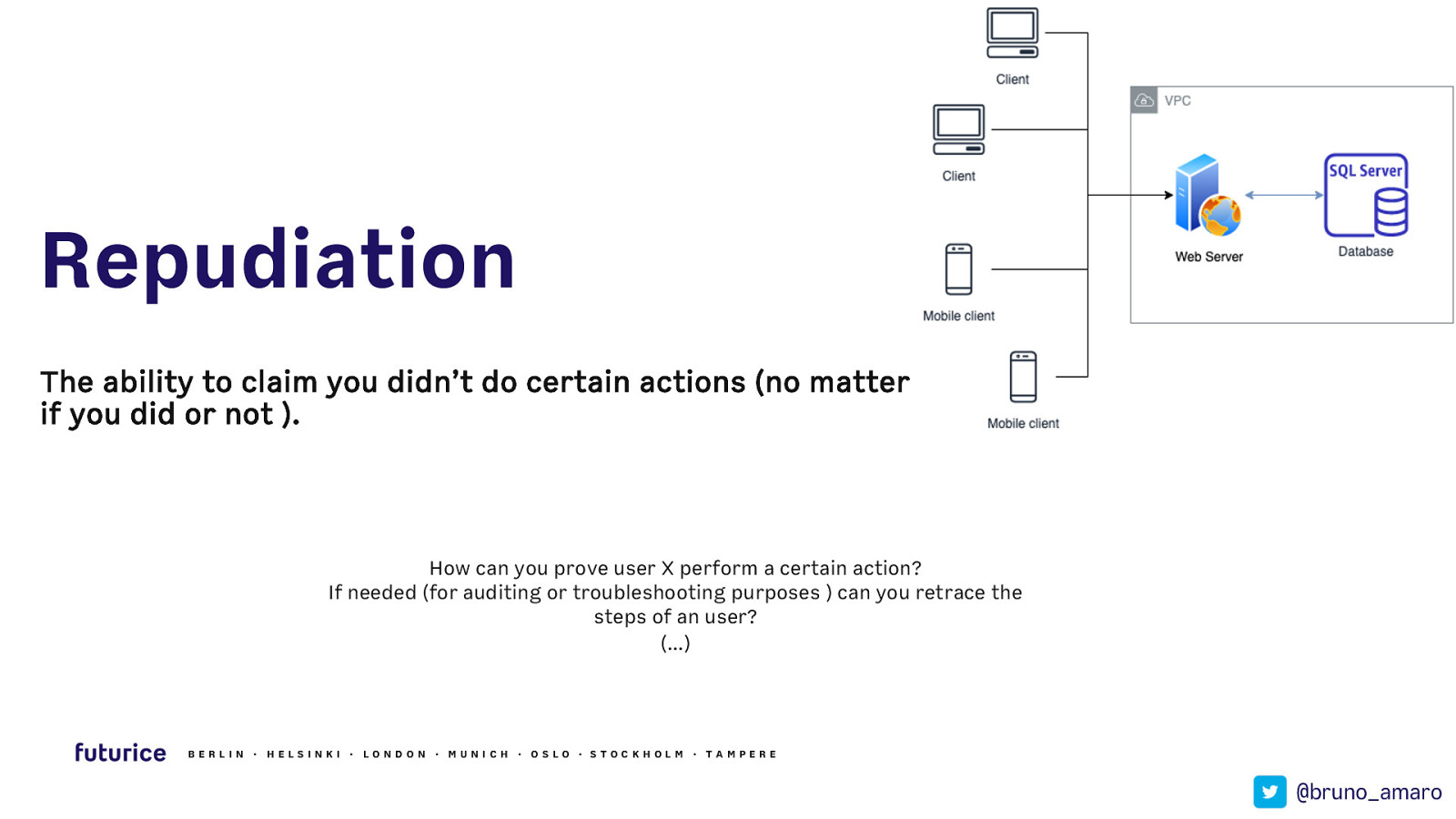
Repudiation The ability to claim you didn’t do certain actions (no matter if you did or not ). How can you prove user X perform a certain action? If needed (for auditing or troubleshooting purposes ) can you retrace the steps of an user? (…) BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 17
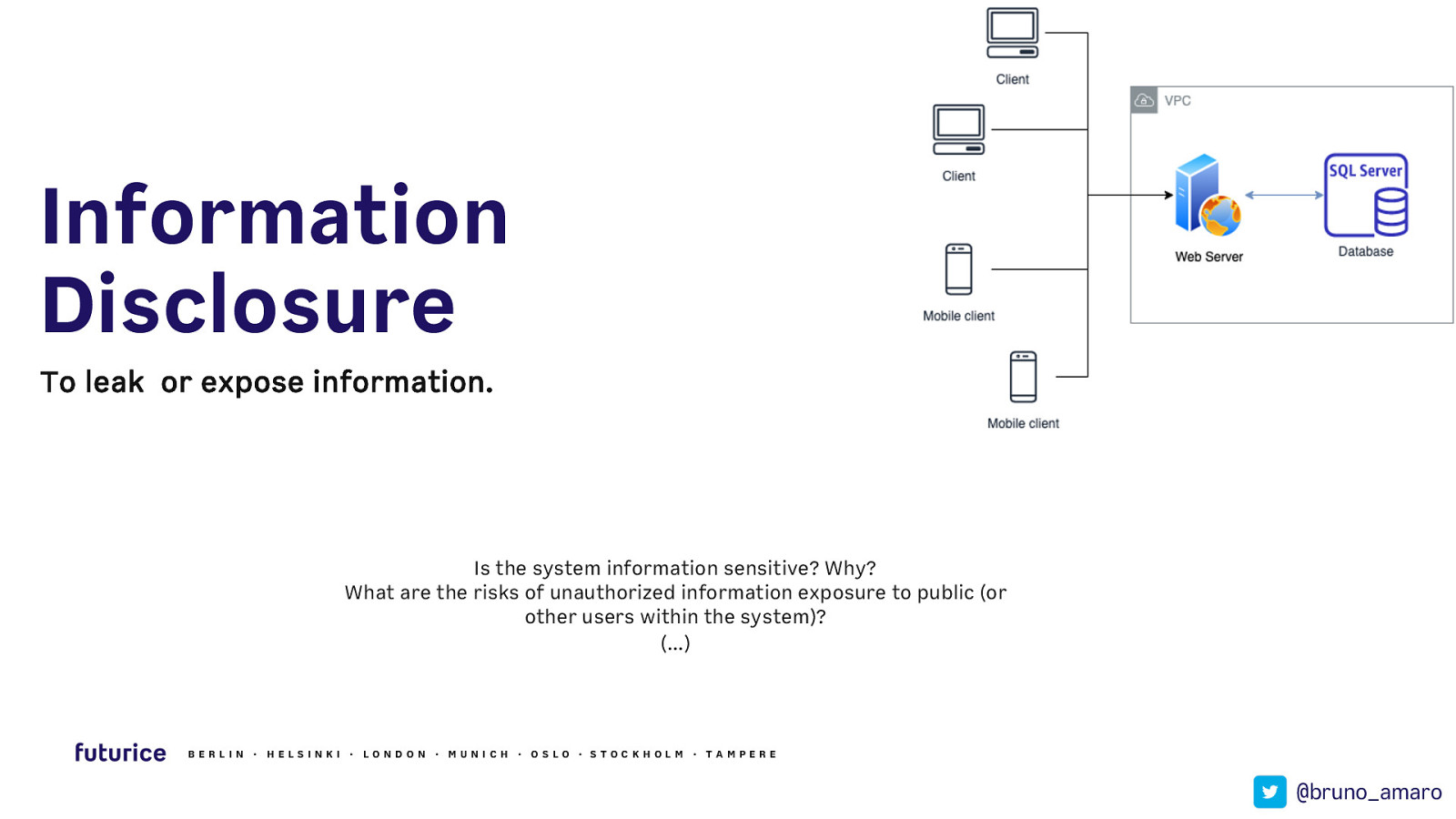
Information Disclosure To leak or expose information. Is the system information sensitive? Why? What are the risks of unauthorized information exposure to public (or other users within the system)? (…) BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 18
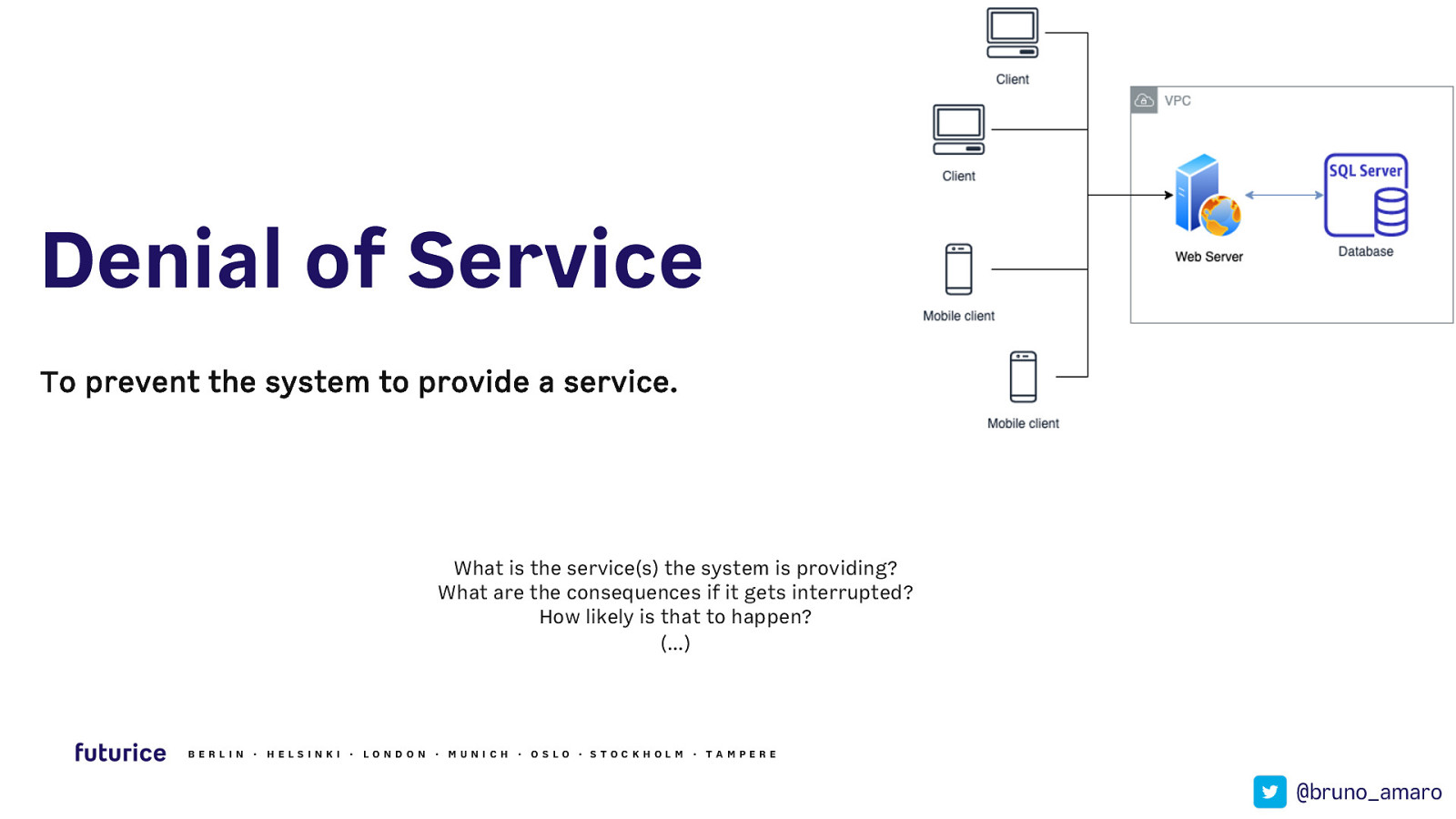
Denial of Service To prevent the system to provide a service. What is the service(s) the system is providing? What are the consequences if it gets interrupted? How likely is that to happen? (…) BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 19

Elevation of Privilege To gain rights to do things you are not suppose to. How could an user escalate to gain admin rights? Can a user with an expired subscription continue to use the service? (…) BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 20
Make it Fun BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE @bruno_amaro
Slide 21

What is the value you create with this? • Security backlog with all the findings and new work uncovered. • Architecture and Flow diagrams up-to-date • Security and Compliance (e.g. PIA for GDPR, PCI DSS, CCPA, etc) • Alignment within the team • Enhanced visibility Photo by Ricardo Rocha on Unsplash @bruno_amaro
Slide 22
Thank you! Kiitos! Danke! Tack! Bruno Amaro Almeida P RINC IP AL ARC HITE C T & ADV ISOR Cloud, DevOps, Security, Data Engineering & AI Reach out on: @bruno_amaro @brunoamaroalmeida BERLIN · HELSIN K I · LON DON · MUN ICH · OSLO · STOCK HOLM · TAMPERE